Digital ad fraud isn’t just growing. It’s evolving.
While industry reports cite losses approaching $100 billion annually, the real damage runs deeper. Fraudsters aren’t just stealing budgets—they’re corrupting attribution data, undermining optimization efforts, and destroying campaign intelligence.
Traditional verification tools have fallen behind. They’re fighting yesterday’s fraud with outdated technology. Server-side verification, limited testing centers, and basic bot detection simply cannot keep pace with increasingly sophisticated fraud techniques.
The solution requires a fundamental shift in verification methodology. Enter residential proxy networks—the missing layer that brings ad verification into the modern era by enabling real-world, geographically accurate monitoring across the actual devices and networks where your ads should appear.
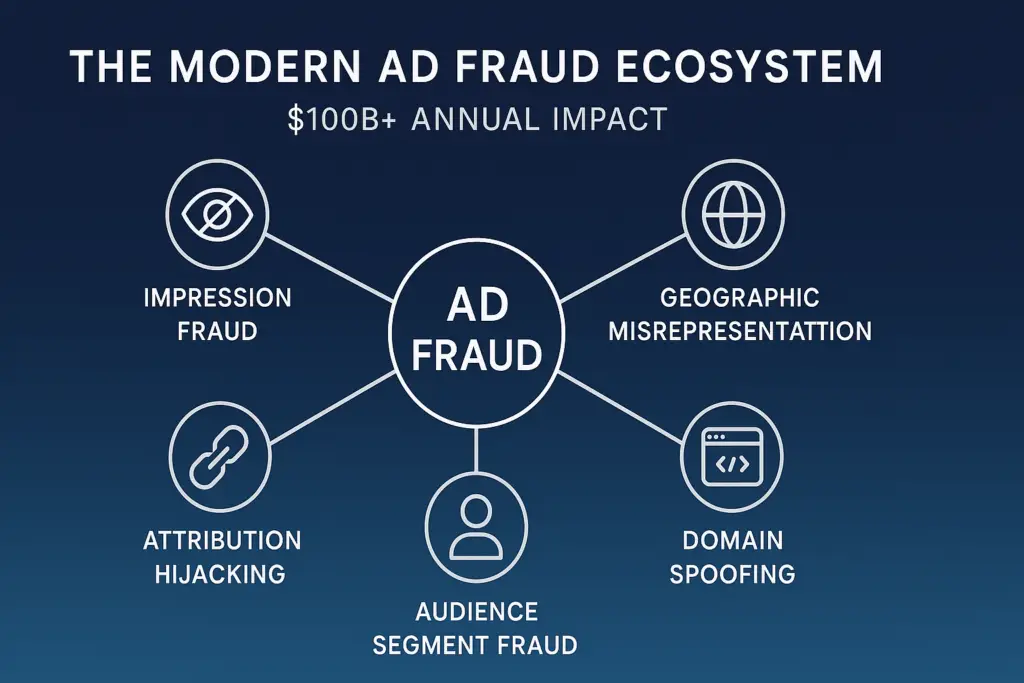
The modern ad fraud ecosystem
Today’s ad fraud operations bear little resemblance to the crude click farms and simple bots of the past. They’ve evolved into sophisticated criminal enterprises with technical capabilities that often exceed those of the advertisers they target.
Modern fraud schemes employ these primary attack vectors:
Sophisticated impression fraud has moved beyond simple invisible ads. Fraudsters now use dynamic resizing, strategic refreshing, and layered iframes to generate impressions that pass basic verification while remaining unseen by users.
Geographic misrepresentation allows publishers to sell premium geo-targeted inventory (US, UK, Germany) while actually serving impressions in lower-value regions. This technique exploits the gap between server-side location data and actual user locations.
Domain spoofing has evolved from basic URL manipulation to complex synthetic site networks that mimic legitimate publisher content while injecting hidden ad slots. These operations create convincing facades that fool both verification tools and human reviewers checking only screenshots.
Attribution hijacking intercepts conversion credit through strategic click injection, timestamp manipulation, and view-through attribution exploitation. This diverts credit from legitimate marketing channels to fraudulent ones.
Audience segment fraud fabricates valuable user segments through manipulated behavioral signals and falsified demographic data. This technique targets the premium CPMs paid for specialized audience segments.
The economic impact extends beyond direct budget theft. Corrupted attribution data leads to fundamentally flawed optimization decisions that can derail entire marketing strategies. Bad data creates bad decisions that create more bad data—a destructive cycle that compounds over time.
The verification gap in contemporary adtech
Current verification systems suffer from fundamental limitations that leave advertisers exposed.
Server-side verification provides false confidence. It evaluates ads from centralized servers rather than actual user environments. This approach may confirm an ad was served to a device in a location, but not whether it appeared correctly on the intended device in the specific targeted geography.
Geographic verification faces particular challenges. Most verification services operate from limited testing centers in major markets. This creates massive blind spots for campaigns targeting diverse or specific geographic areas. A verification service without actual measurement points in target regions cannot validate geo-targeting accuracy.
The most critical gap involves the client-side reality. Ads behave differently across various ISPs, device types, browser configurations, and user contexts. Centralized testing simply cannot reproduce this diversity. You’re verifying a simulated approximation rather than the actual user experience.
This verification gap creates the perfect environment for sophisticated fraud to flourish undetected.
Residential proxies are the missing verification layer
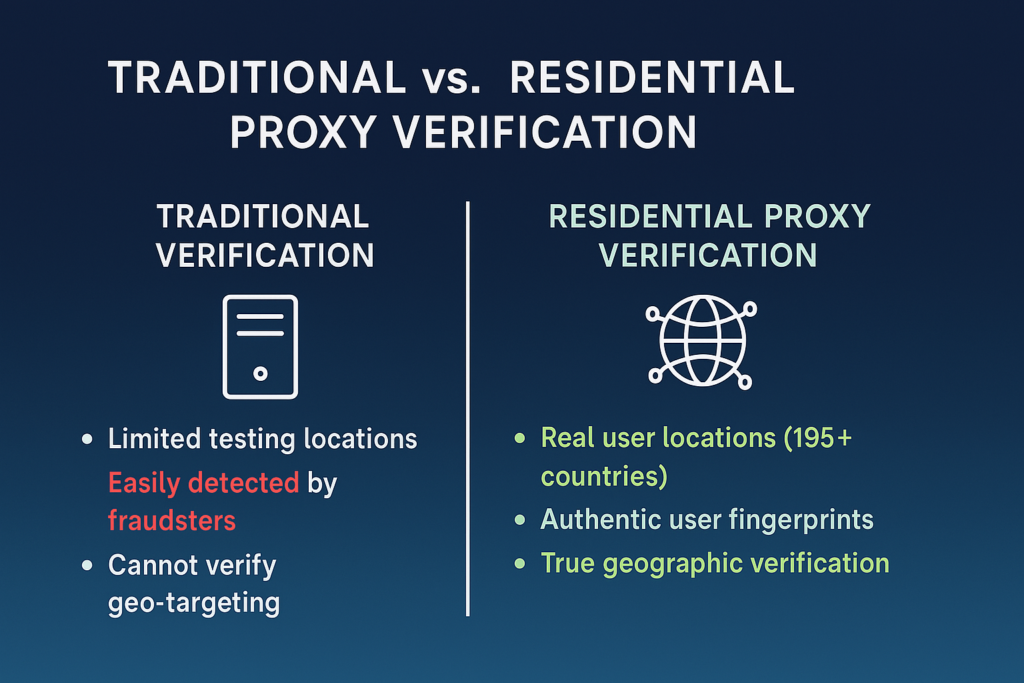
Residential proxies provide the missing piece for comprehensive ad verification. But what are they exactly?
Unlike datacenter proxies (which operate from obvious commercial IP ranges), residential proxies route traffic through actual household connections provided by regular Internet Service Providers. Mobile proxies similarly use real mobile carrier networks. These proxies reflect genuine user connection profiles.
This distinction is CRITICAL for ad verification. Here’s why:
True geographic presence. Residential proxies offer authentic local connections in over 195 countries and thousands of cities. This allows verification from the exact locations specified in campaign targeting parameters—not just approximations from the nearest testing center.
ISP diversity. Different Internet Service Providers may handle ad content differently due to network configurations, caching systems, and peering relationships. Residential proxies provide access across the full spectrum of ISPs in each market, revealing delivery inconsistencies invisible to centralized testing.
Authentic device fingerprints. Residential connections naturally carry the typical browser configurations, connection characteristics, and user-agent profiles of actual users in each region. This allows verification systems to present as legitimate viewers rather than obvious testing tools (which sophisticated fraud systems can detect and circumvent).
Natural traffic patterns. Residential IPs display the expected usage patterns of real users. This prevents triggering the increasingly common “verification detection” mechanisms that fraudulent operations use to identify and misdirect verification attempts.
For verification purposes, ethically-sourced residential proxies are non-negotiable. This means clear consent mechanisms, transparent compensation models, and strict usage limitations. Ethical considerations aside, proper sourcing ensures stable, reliable verification infrastructure.
Building advanced verification systems
Implementing residential proxy verification requires thoughtful architecture design. Here’s the fundamental approach used by successful verification operations:
The foundation begins with geographic precision. Effective verification requires exact location matching to campaign parameters. This means capabilities for country, state/region, city, and even ZIP code targeting that correlate precisely with campaign settings.
The proxy rotation strategy must balance two competing requirements. First, it needs enough variability to prevent pattern recognition by fraud detection systems. Second, it must maintain consistent measurement points for reliable trend analysis. The optimal approach involves stable proxy groups for baseline measurements supplemented by rotating proxies for broader coverage.
Authentication systems must maintain enterprise-grade security while supporting distributed verification nodes. Advanced implementations use API-based authentication rather than username/password combinations, with request signing mechanisms that prevent credential exposure.
For integration with existing platforms, modern verification systems employ a dual approach:
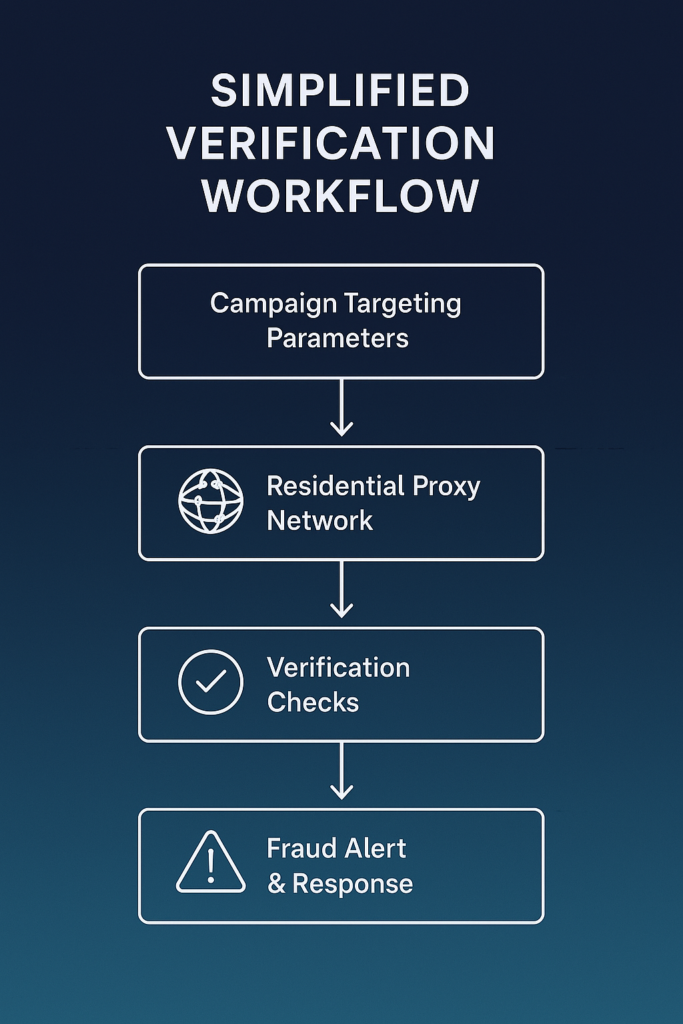
Direct measurement through custom verification scripts that execute within the proxy environment
Browser automation that captures the complete rendering environment including visual confirmation
This combination provides both code-level verification and visual validation—essential for detecting sophisticated fraud techniques that specifically target verification systems.
Scale considerations vary dramatically based on campaign size and targeting complexity. A reasonable starting point allocates:
- One verification node per targeted metropolitan area
- Verification frequency of 3-5 times daily per creative variant
- Increased frequency for high-value placements and premium inventory
The logging infrastructure must capture comprehensive evidence including:
- Full HTTP request and response cycles
- Rendered DOM snapshots
- Visual captures with timestamp verification
- Network performance metrics
- Execution environment details
This evidence becomes essential for remediation with partners and potential contractual enforcement actions when fraud is detected.
Real-world verification protocols
Implementing verification requires systematic processes across the campaign lifecycle:
Pre-campaign baseline establishment begins 7-10 days before launch. This phase identifies normal performance patterns and potential red flags in targeted inventory. The baseline should include:
- Typical ad render times across regions and publishers
- Standard viewability metrics for similar placements
- Expected audience segment distribution
- Regular delivery patterns throughout the day
In-flight monitoring operates continuously during campaigns with alert systems for anomaly detection. Effective systems monitor:
- Sudden changes in performance metrics
- Geographic delivery inconsistencies
- Unusual impression clustering
- Render time anomalies
- Viewability deviations
- Suspicious click patterns
Post-campaign audit procedures compare actual delivery against contracted terms, identifying discrepancies that warrant compensation or future inventory adjustments.
Detection triggers should be calibrated to campaign-specific thresholds rather than generic standards. Verification from residential proxies provides sufficient data fidelity to establish precise baseline metrics for each placement type and region.
False positive mitigation requires human review of flagged incidents before partner notification. This review should follow a standardized evaluation protocol that distinguishes between technical glitches, implementation errors, and actual fraud attempts.
When fraud is identified, documentation must meet evidence standards that support contractual remedies. This typically includes:
- Multiple verification timestamps showing consistent issues
- Verification from different proxy sources confirming the problem
- Comparison with control measurements from verified legitimate impressions
- Complete technical logs demonstrating the methodology
This evidence supports remediation conversations with partners and, when necessary, provides the foundation for contractual enforcement.
The business case for proxy-based verification
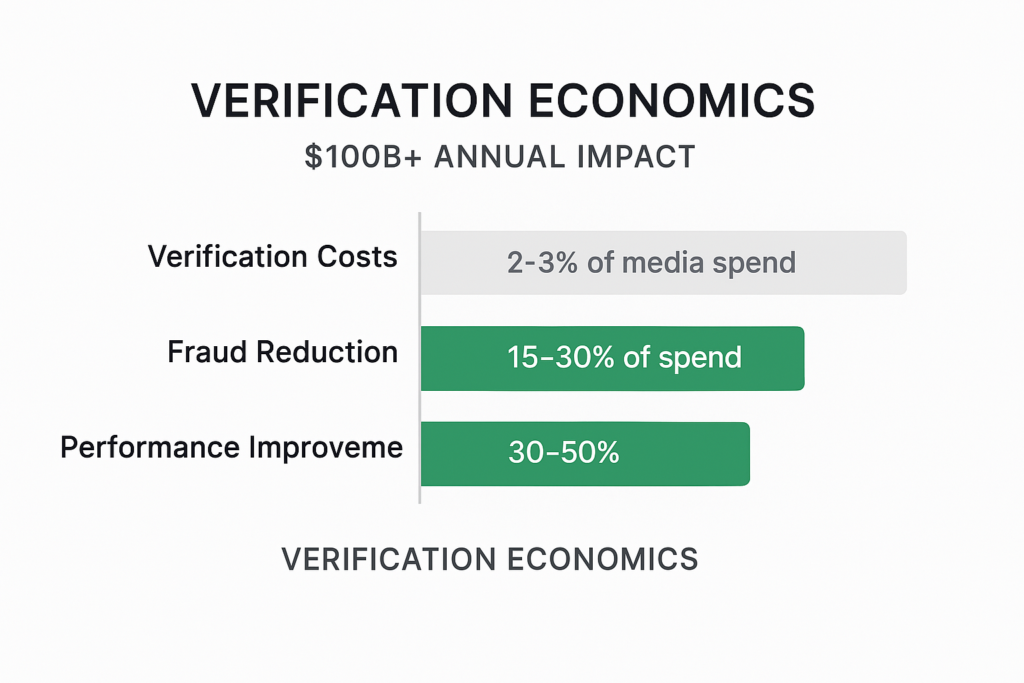
The cost structure for residential proxy verification includes:
- Proxy network access (typically $2,000-5,000 monthly for enterprise-scale coverage)
- Verification platform licensing or development
- Integration engineering
- Ongoing monitoring and analysis
Against these costs, organizations typically see returns in these categories:
Direct fraud reduction. Companies implementing comprehensive verification typically identify and eliminate 15-30% of fraudulent impressions that bypass traditional verification. For a $1M monthly ad spend, this alone represents $150,000-300,000 in recovered media value.
Attribution accuracy improvement. When fraud corrupts attribution data, marketing decisions become fundamentally flawed. Organizations implementing advanced verification report 20-40% changes in channel attribution, revealing previously hidden high-performers and exposing fraudulent conversion claims.
Media efficiency gains. With accurate performance data, optimization improves dramatically. Verification-driven optimization typically yields 30-50% performance improvements in verified channels compared to previous baselines.
The cost of inaction compounds over time. Unchecked fraud not only steals immediate budget but corrupts the data driving future decisions. This creates a downward spiral of decreasing performance as optimization decisions based on fraudulent data lead to increasingly poor outcomes.
For most enterprise advertisers, the investment scaling follows a simple formula:
Basic verification: 1-2% of media spend Comprehensive verification: 2-3% of media spend High-security verification (finance, pharma): 3-5% of media spend
Organizations typically start with high-value campaigns before expanding coverage across their full media investment.
Future verification innovations
The verification landscape continues to evolve, with several promising developments emerging:
Machine learning integration is moving beyond simple pattern recognition to predictive fraud identification. These systems analyze thousands of variables to identify subtle fraud signals before they become obvious problems.
Automated response systems can now modify campaign parameters in real-time when fraud is detected, rerouting budget to verified safe inventory without human intervention.
Cross-platform verification coordination shares fraud signals across advertisers, creating network effects that make fraud increasingly difficult to sustain. These collaborative systems maintain advertiser anonymity while leveraging collective intelligence.
Publisher-side integration is bringing verification directly into trusted publisher environments, creating audit trails that start at the inventory source rather than solely from the advertiser side.
For organizations implementing verification today, these innovations represent future enhancements to systems that deliver immediate value in their current form.
Getting started with ad verification proxies
Organizations new to advanced verification should follow this implementation sequence:
- Provider selection based on geographic coverage, ethical sourcing practices, and enterprise security capabilities. IPBurger offers industry-leading residential proxy coverage across 195+ countries with the 99.95% uptime essential for consistent verification.
- Pilot program development focusing on high-value campaigns with clear measurement criteria. Ideal candidates include:
- Geographically targeted campaigns
- High-CPM placements
- Performance campaigns with conversion tracking
- Brand campaigns on unfamiliar inventory
- Implementation team assembly including technical integration specialists, media buyers who understand campaign parameters, and analysts who can interpret findings and recommend actions.
- Staged rollout beginning with parallel verification alongside existing methods, then gradually shifting reliance to the more comprehensive system as confidence builds.
- Performance measurement that quantifies both fraud reduction and performance improvements attributable to better data quality.
As verification uncovers issues, the natural response is expanding coverage. Most organizations begin with 20-30% of their highest-risk inventory before expanding to comprehensive coverage.
In today’s sophisticated fraud environment, advanced verification isn’t a luxury—it’s an essential component of media efficiency. Without knowing what’s actually happening with your ads across the internet, optimization becomes a game of chance rather than a data-driven discipline.
Ad verification proxies provide the missing layer of certainty in an increasingly uncertain digital landscape.
FAQs
How do residential proxies differ from datacenter proxies for verification?
Residential proxies route through actual household ISP connections, presenting as legitimate users with authentic IP characteristics. Datacenter proxies use commercial IP ranges that sophisticated fraud operations can easily identify and circumvent by showing different content to these obvious verification attempts.
What geographic coverage is necessary for effective verification?
Coverage should match your campaign targeting exactly. If you’re targeting 50 specific cities, your verification should operate from those exact locations—not approximations from the nearest major market where a traditional verification provider might have a presence.
How often should verification checks run?
For standard campaigns, 3-5 daily verification cycles per creative variant provide sufficient coverage to identify issues without excessive cost. High-value placements and suspicious inventory warrant increased frequency, potentially hourly for mission-critical campaigns.
Can publishers detect and circumvent proxy-based verification?
Sophisticated fraud operations can sometimes detect basic proxy implementations. This is why enterprise verification requires residential proxies with authentic user characteristics rather than obvious datacenter IPs. When properly implemented, residential proxy verification presents identically to legitimate user traffic.
How does proxy verification integrate with existing verification platforms?
Most organizations adopt a multi-layer approach, maintaining their existing verification while adding proxy-based systems for enhanced capabilities. Modern verification platforms offer API integration that incorporates data from multiple sources into unified reporting.
What’s the typical timeframe for implementation?
Basic implementation can be completed in 2-3 weeks. Comprehensive integration with custom alerting and response protocols typically requires 6-8 weeks. Organizations usually begin seeing actionable fraud reduction opportunities within the first monitoring cycle.How does IPBurger ensure the ethical sourcing of residential proxies?
IPBurger’s residential network uses explicit opt-in processes with clear terms and fair compensation models. Their compliance infrastructure ensures appropriate usage boundaries and transparent consent mechanisms—essential considerations for enterprise verification deployments.